Signed with a valid Apple ID, Backdoor:Python/Janicab.A uses a Unicode trick to pass as a standard document instead of an application.
F-Secure is reporting that some new malware attempts in OS X are using a spoofing technique to disguise malicious installations as standard files. The technique involves using a special Unicode character in file names that will make an application appear to be a standard document file.
While applications can be renamed with ".doc" or ".pdf" extensions in the OS X Finder, the system will append the ".app" extension to show only the name has been altered and the file is still recognized as a program. This will happen even if you have the Finder set to hide file extensions.
Of course, you can use the Terminal and some other services to change the name from ".app" to ".doc" or something else; however, doing so will break the functionality of the application package and make it appear as a standard folder.
To get around this, if you wanted to disguise a file, you could use the Unicode character "U+202e" to override the system's automatic compensation for the name change, and keep the .app extension hidden while showing only the fake one. For example, copy an application such as TextEdit to your Desktop, and then edit its name to append ".pdf" to the end of it. When you do so, the system will append ".app" to the name as expected. Now remove the change so the name appears only as "TextEdit" with no extensions.
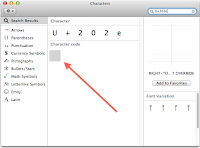
Following reverting the name, enable the OS X Character Viewer and activate the panel from the input menu. With the panel open, search for "U+202e" to find the "Right-to-left" character. This will not show up as a symbol, but can be selected and input at the point of the cursor as a character. With this character ready, you would follow these steps:
1. Select TextEdit and press Enter to edit its name.
2. Move your cursor to the end and type a period to begin the suffix.
3. Double-click the hidden "U+202e" character in the Character Viewer panel to enter it.
4. Type "fdp" or "cod" ("pdf" and "doc" backward).
5. Press Enter again to apply the name change.
When you do this, the TextEdit application will assume the ".pdf" extension, but still maintain its status as a valid application bundle with the .app extension hidden. This results in a file that appears to be a PDF by extension, but which will still have a hidden .app extension and will run as an application when opened.
Overall, this way of disguising programs does not constitute much of a threat, especially if you have Apple's Gatekeeper feature set to allow only programs from the App Store or an approved developer ID to run; however, F-Secure outlines that this spoofing technique has been found in recent malware that is signed with a valid Apple developer ID.
F-Secure has given the new malware the name Backdoor:Python/Janicab.A. Using the technique described above, it tries to disguise itself as a file other than an application bundle. When run, the malware will open a decoy PDF document, and then create a "cron" entry to automatically launch Python scripts that attempt connections to remote command-and-control servers. The malware then attempts to upload screenshots and audio recordings to these servers.
This setting will ensure that all programs except those vetted by Apple's App Store team will be prevented from running the first time if you open them in the Finder. To open them, you will have to right-click them and choose "Open," followed by confirming you want to do this, and then authenticating to add an exception for this program to the Gatekeeper rules. Alternatively, you can set up custom Gatekeeper rules manually to accommodate other applications.


No comments:
Post a Comment