from BetaNews.com
Security researchers at Sophos Labs last week discovered a new, "still in beta" backdoor Trojan targeting Mac OS.
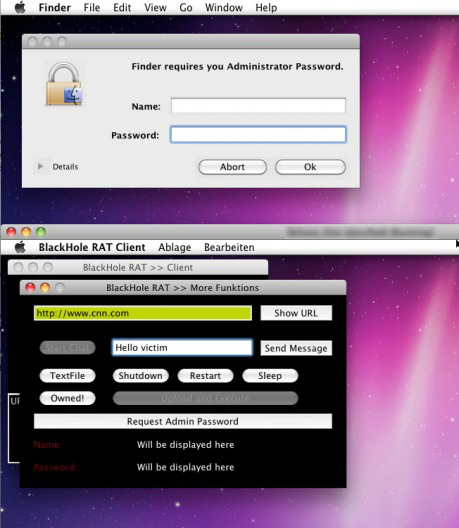
The Trojan, identified as BlackHoleRAT, is a variant of the free "remote administration tool" darkComet RAT for Windows, and gives the administrator the ability to place text files on the desktop, send restart, shutdown or sleep commands, to run shell commands, to place a full-screen window with a message that forces a reboot, to force URLs to a client, and to pop up a fake "Administrator Password" phishing window.
It lacks much of the functionality of its Windows counterpart, but carries the somewhat amusing message with the forced reboot:
I am a Trojan Horse, so i have infected your Mac Computer. I know, most people think Macs can't be infected, but look, you ARE Infected! I have full controll over your Computer and i can do everything I want, and you can do nothing to prevent it. So, Im a very new Virus, under Development, so there will be much more functions when im finished.
Obviously this pseudo-apologetic message is geared toward potential customers who would like to sink their teeth into Mac OS malware, rather than actually for someone whose system was infected.
It's a little boring but you can watch the video HERE
Since Mac OS has been gradually gaining PC operating system market share, more companies are entering the Mac security field. Earlier this month Comodo released a free Mac antivirus alongside Sophos.
--------------------------
And that's just in Beta! You know most Mac users think they don't need protection so imagine what the final product will do to all the vulnerable Macs out there in the world.
Monday, February 28, 2011
“Bad Apple” Antenna Infects Verizon iPhones Too!
from ReviewsofEclectronics.com
Consumers were hopeful when Verizon announced they would be carrying the long-awaited iPhone 4. Previously, the iPhone had only been carried by AT&T, but Verizon has long been lauded for its stellar reception, and there were reports of problems with the AT&T’s iPhone antenna. Hoping that this problem might be resolved, customers bravely purchased the Verizon iPhone-but unfortunately, it appears as though Apple has done nothing to remedy the problem.
 Still, Apple claims to have fixed the “non-existent” problem in Verizon’s iPhone. Apple did indeed make superficial, minor changes to the antenna on the Verizon iPhone. However, the problem still remains; while dissecting the phone it appears that there is an extra gap in the cellular band, which is intended to lessen the probability of dropping a call, but it is clear that the issue has not been addressed correctly. According to Consumer Reports, the Verizon iPhone “shares with its sibling the possibility of compromised performance in low-signal conditions when used without a bumper or case.”
Still, Apple claims to have fixed the “non-existent” problem in Verizon’s iPhone. Apple did indeed make superficial, minor changes to the antenna on the Verizon iPhone. However, the problem still remains; while dissecting the phone it appears that there is an extra gap in the cellular band, which is intended to lessen the probability of dropping a call, but it is clear that the issue has not been addressed correctly. According to Consumer Reports, the Verizon iPhone “shares with its sibling the possibility of compromised performance in low-signal conditions when used without a bumper or case.”
Consumers were hopeful when Verizon announced they would be carrying the long-awaited iPhone 4. Previously, the iPhone had only been carried by AT&T, but Verizon has long been lauded for its stellar reception, and there were reports of problems with the AT&T’s iPhone antenna. Hoping that this problem might be resolved, customers bravely purchased the Verizon iPhone-but unfortunately, it appears as though Apple has done nothing to remedy the problem.
Why would Apple choose not to fix this? They surely had ample time to; the antenna problems on the iPhone were manifested from the start. Unfortunately, the “death grip” remains an issue. If you are unfamiliar with the term, it refers to the problem that first appeared when iPhones were initially launched. Consumers found that holding their iPhones on a specific part of the edge caused dropped calls or lack of a connection, period. For a lot of people, it was natural to hold their device in this fashion, and so there were many complaints about why this was happening. Apple’s response to all of this was to deny all responsibility of the problem. Steve Jobs even declared that consumers were holding the phone the “wrong way”!
 Still, Apple claims to have fixed the “non-existent” problem in Verizon’s iPhone. Apple did indeed make superficial, minor changes to the antenna on the Verizon iPhone. However, the problem still remains; while dissecting the phone it appears that there is an extra gap in the cellular band, which is intended to lessen the probability of dropping a call, but it is clear that the issue has not been addressed correctly. According to Consumer Reports, the Verizon iPhone “shares with its sibling the possibility of compromised performance in low-signal conditions when used without a bumper or case.”
Still, Apple claims to have fixed the “non-existent” problem in Verizon’s iPhone. Apple did indeed make superficial, minor changes to the antenna on the Verizon iPhone. However, the problem still remains; while dissecting the phone it appears that there is an extra gap in the cellular band, which is intended to lessen the probability of dropping a call, but it is clear that the issue has not been addressed correctly. According to Consumer Reports, the Verizon iPhone “shares with its sibling the possibility of compromised performance in low-signal conditions when used without a bumper or case.”Does Apple plan to improve the antenna for the iPhone 5 or will the problem remain? It looks like we will have to wait and see, as the issue is clearly not fixed for the Verizon iPhone.
----------
A network, like a chain, is only as strong as it's weakest link. In this case it's Apple!
Thursday, February 10, 2011
iPhone Security Breach Gives Hackers Access To Your Private Data
from MobileCrunch.com
Researchers in Germany (from the Fraunhofer Institute, the same place that brought us the MP3) have deduced a method to retrieve, without your authorization, all of your iPhone’s secrets. Passwords, that is. And it only takes six minutes. Oh dear.
The attack, which requires physical access to the iPhone (i.e. the attack cannot be done remotely), reveals user passwords and other sensitive information. The phone is jailbroken, then a series of scripts are run that effectively circumnavigate the phone’s encryption. (Note that the encryption isn’t actually broken in this attack.) Passwords for things like e-mail accounts and Wi-Fi networks are readily available to the attacker. And once the attacker has your e-mail account credentials, what’s to stop him from requesting your Facebook or Twitter password be reset? Bam, now he has that, too.
The glitch affects all iOS devices running the latest firmware.
What should you do if you lose your iPhone? Your best bet is to change any and all passwords that may have been used on the device: your e-mail, social networks, Amazon, etc. If you’ve logged into a service using the phone then you need to assumed an evildoer will have access to that password.
Incidentally, The iPhone Guru has step-by-step directions on how you can remove your iPhone’s passcode (the “scroll to unlock” one) with just a few pieces of software. You’d be doing this primarily to demonstrate to yourself how puny iPhone security truly is. How about this: keep your phone glued to your person at all times, lest you find yourself in an unenviable situation.
---
Now, I understand that one would need physical access to the phone but how hard is that? I work in an office and I see tons of people that leave their phones on their desks while they are walking around the office, at a meeting or otherwise occupied. I've never hacked someones phone because I'm not that kind of person. Who's to say the next person won't be?
Researchers in Germany (from the Fraunhofer Institute, the same place that brought us the MP3) have deduced a method to retrieve, without your authorization, all of your iPhone’s secrets. Passwords, that is. And it only takes six minutes. Oh dear.
The attack, which requires physical access to the iPhone (i.e. the attack cannot be done remotely), reveals user passwords and other sensitive information. The phone is jailbroken, then a series of scripts are run that effectively circumnavigate the phone’s encryption. (Note that the encryption isn’t actually broken in this attack.) Passwords for things like e-mail accounts and Wi-Fi networks are readily available to the attacker. And once the attacker has your e-mail account credentials, what’s to stop him from requesting your Facebook or Twitter password be reset? Bam, now he has that, too.
The glitch affects all iOS devices running the latest firmware.
What should you do if you lose your iPhone? Your best bet is to change any and all passwords that may have been used on the device: your e-mail, social networks, Amazon, etc. If you’ve logged into a service using the phone then you need to assumed an evildoer will have access to that password.
Incidentally, The iPhone Guru has step-by-step directions on how you can remove your iPhone’s passcode (the “scroll to unlock” one) with just a few pieces of software. You’d be doing this primarily to demonstrate to yourself how puny iPhone security truly is. How about this: keep your phone glued to your person at all times, lest you find yourself in an unenviable situation.
---
Now, I understand that one would need physical access to the phone but how hard is that? I work in an office and I see tons of people that leave their phones on their desks while they are walking around the office, at a meeting or otherwise occupied. I've never hacked someones phone because I'm not that kind of person. Who's to say the next person won't be?
Subscribe to:
Posts (Atom)