Wednesday, December 27, 2017
First Lawsuits Filed Against Apple for Slowing iPhones
Over the years, iPhone owners have often wondered aloud if Apple was doing something to slow down older devices. Now, we know that yes, it does do that. Just a few days after admitting that it has been quietly throttling older iPhones with degraded batteries, a pair of lawsuits have been filed against Apple alleging fraud and deceptive practices.
It became clear during the last few iOS version updates that Apple had opted to apply performance throttling to older devices. It wasn’t until Geekbench ran comparisons with various iOS versions that iPhone owners had any proof. Apple was forced to issue a statement in which is admitted to slowing down iPhones. In some ways, its position makes sense, but the way it handled the situation is terrible.
The situation has to do with how lithium-ion batteries age. We’re all familiar with batteries losing capacity as they get old, but they also have less voltage. It turns out Apple didn’t include enough headroom for the battery, and its voltage can fall below what is needed to power the custom A-series system-on-a-chip. Without enough voltage, the phone can just shut down without warning. Apple’s solution to this was to add performance throttling to iOS based on battery voltage. So, if your battery is degrading, your phone gets slow.
The first class-action lawsuit filed in Illinois accuses Apple of violating the Illinois Consumer Fraud and Deceptive Business Practice Art. Specifically, the filers point to Apple’s decision not to notify users it was going to throttle their phones. As had been pointed out, very few would suspect a battery issue as the root cause of sluggish performance. That could lead consumers just to buy a new phone, which is to Apple’s advantage.
Another suit filed in Los Angeles claims Apple’s phone throttling plan “was never requested or agreed upon.” This suit also suggests Apple is hoping to get consumers to upgrade by slowing down their phones rather than simply reporting that the hardware might need service.
It looks like Apple’s decision to introduce this “feature” secretly is the main issue here. Even if Apple’s intentions were pure (which is certainly up for debate), making these performance changes in secret looks very suspicious. For a company that claims to care about the user experience, this whole fiasco makes Apple look quite disconnected from the concerns of its customers. Class actions like these are notoriously slow to litigate, so iPhone owners might end up with a small settlement in a couple years.
Monday, December 18, 2017
New MacOS malware steals bank log-in details and intellectual property
From https://www.scmagazineuk.com
Security researchers have discovered a new, invasive OSX.Pirrit adware variant targeting Mac OS X that enables cyber-criminals to take full control of a user's Mac computer.
Security researchers have discovered a new, invasive OSX.Pirrit adware variant targeting Mac OS X that enables cyber-criminals to take full control of a user's Mac computer.
The malware has already infected thousands of Mac computers around the world. According to a blog post by Amit Serper, principal security researcher at Cybereason, while usual adware campaigns enable the attackers to flood a person's computer with ads, this malware not only bombards Macs with adware, it spies on users and runs with the highest user privileges, enabling hackers to leverage this adware to capture personal information on the users, including bank account logins and intellectual property of businesses.
“To my surprise, it's very active. Not only is it still infecting people's Macs, OSX.Pirrit's authors learned from one of their mistakes (They obviously read at least one of our earlier reports),” said Serper.
He added that unlike old versions of OSX.Pirrit that used rogue browser plug-ins or even installed a proxy server on the victim's machine to hijack the browser, this incarnation uses AppleScript, Apple's scripting/automation language.
“And, like its predecessors, this variant is nasty. In addition to bombarding people with ads, it spies on them and runs under root privileges,” he said.
Serper said that the malware uses AppleScript to injects JavaScript code directly into the browser. He added that the code is “a great example of how an adtech company is borrowing nefarious tactics found in malware to make it hard for antivirus software and other security products to detect them.”
“There is no difference between traditional malware that steals data from its victims and adware that spies on people's Web browsing and target them with ads, especially when those ads are for either fake antivirus programs or Apple support scams,” he said.
“As for OSX.Pirrit malware, it runs under root privileges, creates autoruns and generates random names for itself on each install. Plus, there are no removal instructions and some of its components mask themselves to appear like they're legitimate and from Apple.”
He said that a company called TargetingEdge created OSX.Pirrit and his research hasn't gone unnoticed by it.
“Cybereason has received a few cease and desist letters from a firm claiming to be TargetingEdge's legal counsel. The letters demand that we stop referring to TargetingEdge's software as malware and refrain from publishing this report,” he said.
Serper said around 28 other antivirus engines on Virus Total also classify it as such. “The authors of this software went through great lengths to mask themselves and distance themselves from it,” he added. TargetingEdge claimed that it develops and operates a “legitimate and legal installer product for MAC users,” and is not malware and doesn't include any features of malware.
Kelvin Murray, threat research analyst at Webroot, told SC Media UK that users need to report any changes to the search or browser settings of their device to the admin. Users need to be aware that these changes can just be one visible part of a much bigger problem. He adds, “In addition, admins need to take the usual security measures including software updates, AV, and user education. Both the admin and users need to see this as yet another sign that Macs are not “virus proof” as is so commonly assumed and often ignored. There is a need of a stronger focus put onto OSX as security vulnerabilities are becoming more apparent, especially taking into account the event of the MacOS High Sierra.”
Sunday, December 17, 2017
Apple refunds Chinese woman after colleague unlocks her iPhone X using Face ID
Chinese Woman Gets Refund From Apple After Colleague Unlocks iPhone X With Face ID
The USP of Apple’s 10th anniversary premium smartphone, iPhone X is the Face ID technology used in the device that provides high security and cannot be tricked, according to the tech giant.
However, this Face ID technology failed when a colleague of a Chinese woman from Nanjing could unlock not one but two of her iPhone X handsets, reported the South China Morning Post.
The woman identified only by her surname Yan, from Nanjing, China told the Jiangsu Broadcasting Corporation that her co-worker was able to unlock both her iPhone X – original as well as the new one Apple gave her as a replacement – on every single attempt.
The first time it happened, Yan called the Apple hotline but the support team apparently refused to believe her. In order to demonstrate the facial recognition problem, Yan went to the nearest Apple Store along with her colleague to show the staff what happened.
Apple staff at the store said the camera might be faulty and gave Yan a refund, which she used to buy a new iPhone X, reported the South China Morning Post. However, she faced the same problem with the replaced iPhone X prompting the store to offer a second refund, said the report.
It’s still not clear whether Yan has bought a third iPhone X with the refund money. Apple has yet to comment on the issue.
Sunday, December 3, 2017
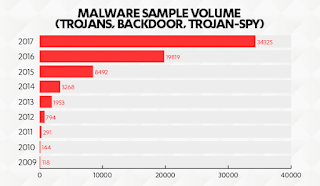
Number of malware attacks on Macs increased by more than 70%
 |
| 70% more malware against Macs |
On October 17, Reuters reported a security breach of the Microsoft Vulnerability Tracking System. A violation that occurred more than four years ago in 2013 . And what was the attack vector related to this security breach? Macs. That these were Macs, our security adviser Sean Sullivan suspected right from the start.
Back in February 2013, he had correctly deduced that Apple Macs were involved in a related hack on Twitter . Given the serious potential damage such hacks could have caused, Sean wrote :
"People who use their Mac for work should not have the same sense of security as home users. It's obvious that work-based Macs are more of a goal, and security expectations should be scaled according to the threat level. "
Nothing about the current Mac threat landscape has led Sean to question his earlier assessment. If you're using a Mac for business, Sean says, "You need to take the time to rethink your security profile."
The latest analysis from F-Secure Labs shows that the new malware is predominantly in the spyware category and over a third of the attacks are targeted attacks. That may not surprise anyone: Macs need protection. However, there are huge differences in how companies have handled the safety of their various endpoints. A quick way to solve this is to opt for cyber security all-round protection, such as Protection Service for Business . The new version includes the advanced XFENCE technology, which provides the next level of Mac security.
Glitch forces iPhones to reboot over and over
NEW YORK – Apple iPhones were rebooting themselves over and over Saturday morning.
Phones across the world running iOS 11 encountered a glitch that triggered at 12:15 a.m. local time. A bug in the 11.1.2 software meant that phones using third-party apps to send recurring notifications, like reminders from work out apps or medical apps, would reboot over and over.
Apple did not respond to a request for comment about the glitch and it’s unclear exactly how many users were affected.
A number of iPhone users took to social media and message boards to learn about the glitch and voice frustrations.
“Looks like i found this late but glad it’s patched. I thought my phone was having a hardware failure, worst iOS bug i’ve ever experienced. This was really bad,” wrote Reddit user KarlKrum.
“This is embarrassing. Facepalm,” wrote Reddit user Siannath.
The company took the unusual step of releasing a software update on a Saturday when it pushed iOS 11.2.
The update fixes the rebooting issue and also includes Apple Pay Cash, the company’s new peer-to-peer payment system, faster wireless charging, and new live wallpapers.
Apple typically releases software updates on Tuesdays.
This is just the latest in a string of glitches for Apple over the past few weeks.
In early November, users encountered an error with its text messaging service in which the device would change a typed lower case “i” into a capital “A.”
Earlier this week developers found a security flaw in the company’s macOS High Sierra computer operating system that allowed users to gain administrative access without inputting a password.
For users still experiencing the rebooting glitch, Apple recommends the following steps.
–Tap Settings > Notifications.
–Tap an app, then turn off Allow Notifications. Repeat this step for each app.
–Update your device to iOS 11.2.
–After updating, tap Settings > Notifications and turn Allow Notifications on again for each app.





