from arstechnica.com
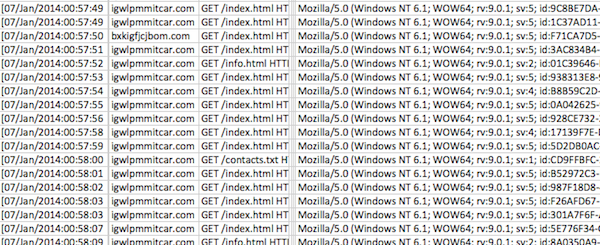
A screenshot of an Apache Server log showing infected Macs connecting to a Flashback command and control server. The user agent strings and referrer strings showing Windows NT 6.1 machines, are set by Flashback. Intego has confirmed that the machines are, in fact, infected Macs.The Flashback trojan that hijacked well over 500,000 Macs at its peak is still clinging to life, with about 22,000 infected machines in recent days, a security researcher said.
The compromised Macs were observed connecting to command and control servers that had been "sinkholed—meaning taken over for research or security purposes—by analysts from security firm Intego. During a five-day period ending January 7, 22,000 Flashback-infected computers reported to server domains recently acquired by Intego, Arnaud Abbati, a researcher with the company, wrote in a blog post. Those machines could be maliciously controlled by anyone who has access to one of the many domain names programmed into a Flashback algorithm, assuming they know how the internals of the malware works.
Flashback first came to light in 2011 when it took hold of people's machines by masquerading as a legitimate installer of Adobe's ubiquitous Flash media player. By early 2012, Flashback morphed from a socially engineered threat to one that performed surreptitious drive-by attacks by exploiting vulnerabilities in Oracle's Java software framework. Flashback was among the most sophisticated pieces of malware ever to target mainstream Mac users.
Self-encryption made it tough for researchers to reverse engineer or hijack the malware. Flashback was used primarily as a "click fraud" tool that caused infected Macs to view sponsored links that had the potential to generate millions of dollars in fraudulent ad revenue. It also had the ability to do much more, including sending spam, engaging in denial-of-service attacks, or logging passwords. Ars has published articles showing how to detect and remove Flashback here and here.
One Flashback capability included the ability to periodically generate a new set of domains that infected Macs would report to. To prevent Flashback operators from losing control of their machines, the malware was programmed to check a new pseudo-randomly generated domain each day in five separate top-level domains (TLDs). In an e-mail, Abbati explained:
"An infected Mac tries to contact the same domain on five TLDs (.com, .net, .info, .in, .kz) until it finds one correct bot response. To block that chain you can't just buy the .com; there is a chance the hacker will test for all TLDs and purchase and use the others for malicious activity. The process is that the server answers back the infected Mac with a secret data to prove that it is a Flashback botnet controller. After that handshake, the network packets are encrypted with the unique identifier given by the infected Mac on the first request to the C&C server. Then the server sends commands over the network to execute on the infected Mac, commands that can be: update your code with an external executable (by downloading it), execute a system command, launch a process, send local files from the infected Mac, etc. To resume, after the handshake with the secret data, the botnet server has a full control against the infected Mac."
Abbati went on to say that Apple countered the threat by reverse engineering the domain-generation algorithm and buying all of the names through the end of 2013. That prevented him or anyone else outside of Apple from monitoring the Flashback botnet. Then, at the beginning of the year, Apple briefly allowed those domain name registrations to expire failed to purchase some domain names, making it possible once again for Intego to peer into the inner workings of Flashback. Over the past few days, Apple has bought all of the 2014 domains. Abbati said that's a good thing for the safety of those who remain infected.
"With the number of computers still infected," he explained, "it’s conceivable that someone with malicious intent could also crack the algorithm, buy the domains, and use them to instruct the computers into nefarious action."

No comments:
Post a Comment